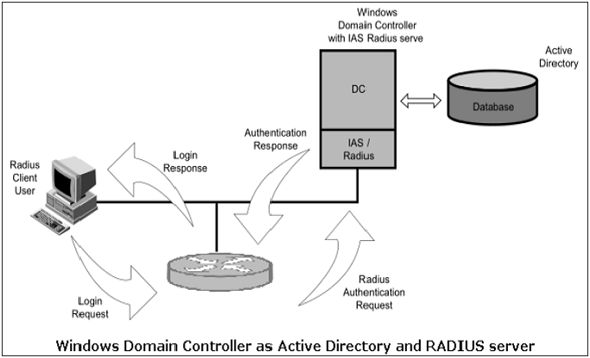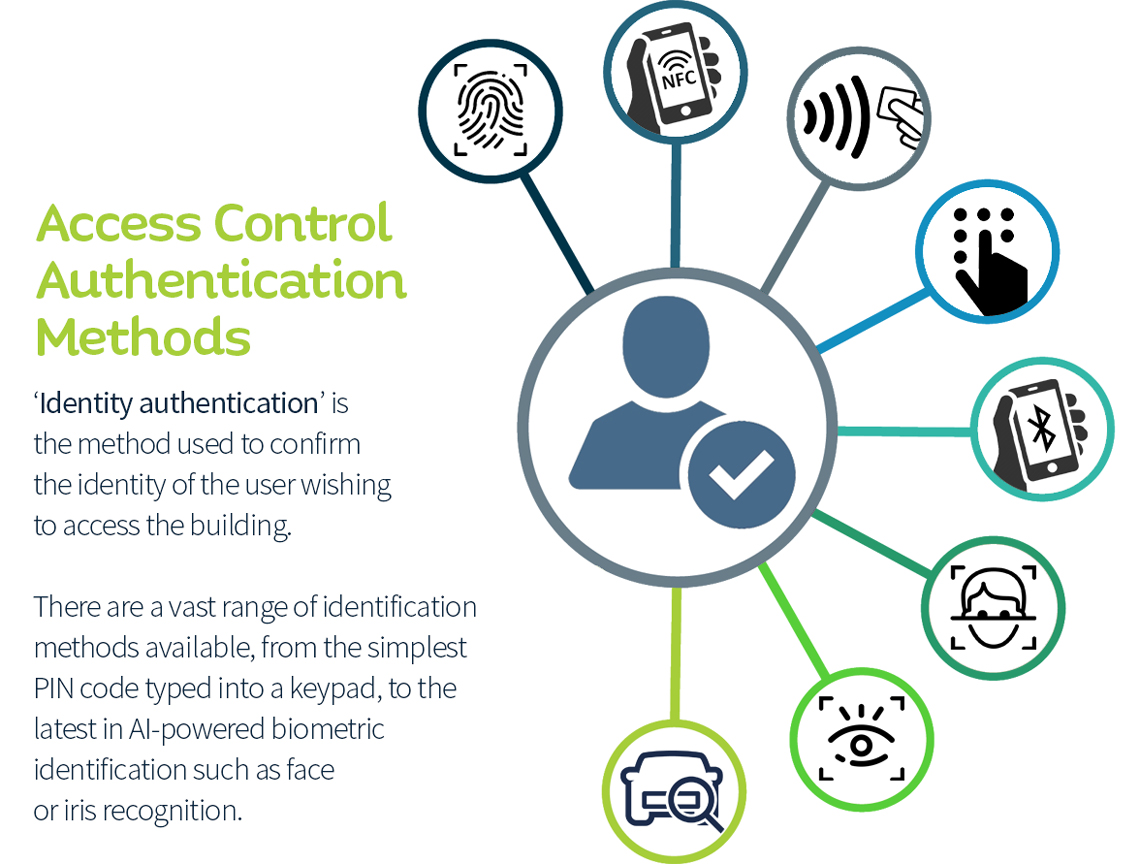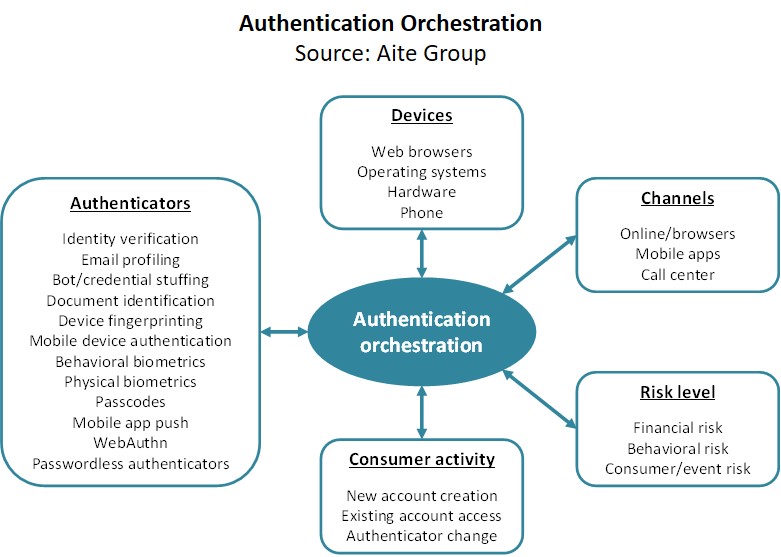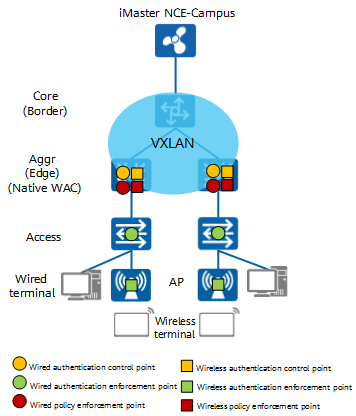
Access Control Design - CloudCampus Solution V100R019C10 Deployment Guide for Large- and Medium-Sized Campus Networks (Virtualization Scenario) - Huawei

Cloud Security Considerations: Authentication / Access Control and Account Privileges - Accudata Systems
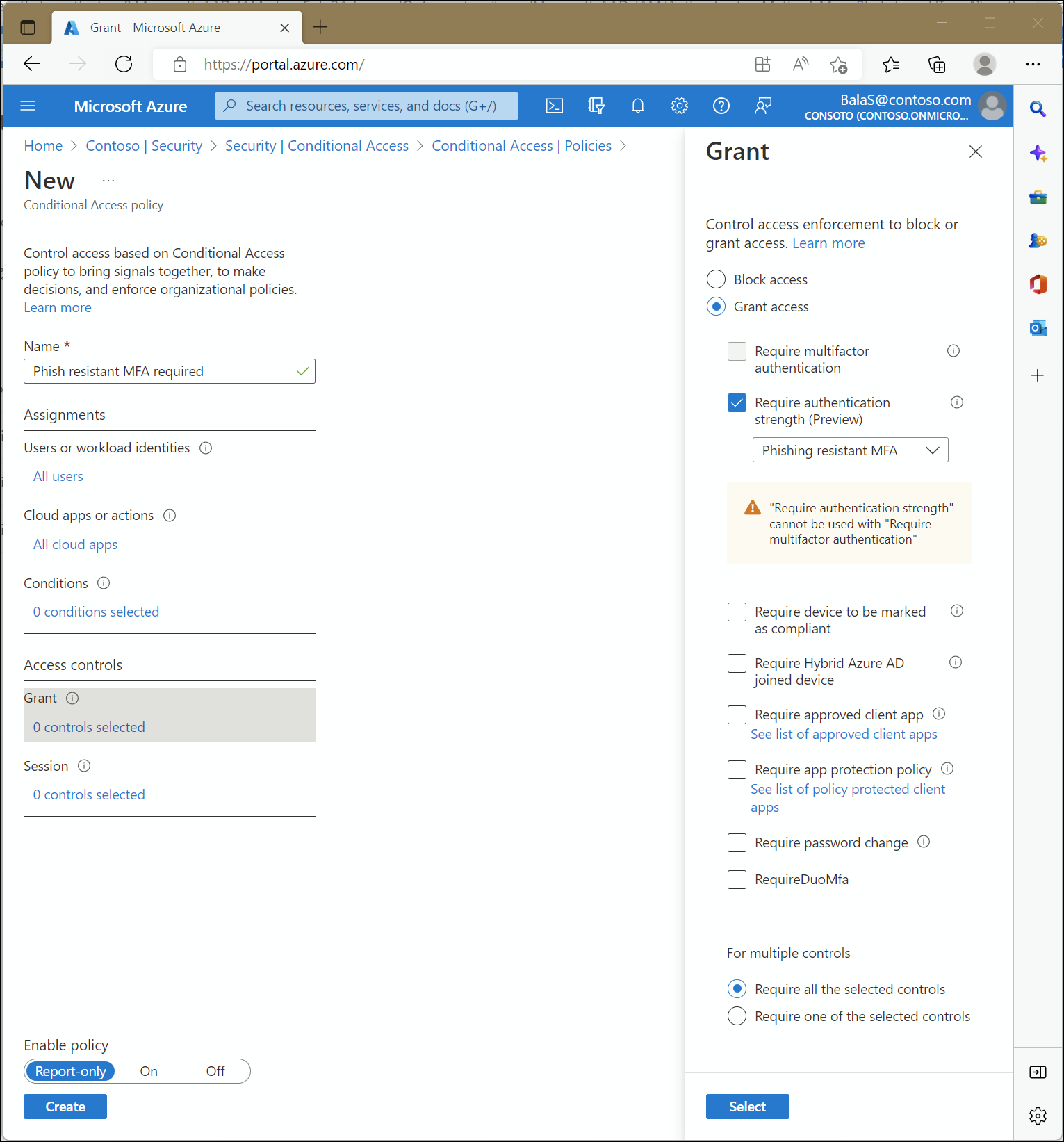
Overview of Azure Active Directory authentication strength (preview) - Microsoft Entra | Microsoft Learn
Authentication and Access Control Use Case Diagram for Cloud-based C4I... | Download Scientific Diagram

Sensors | Free Full-Text | Protocol-Based and Hybrid Access Control for the IoT: Approaches and Research Opportunities


![Access Control Process - Access Control and Identity Management, 3rd Edition [Book] Access Control Process - Access Control and Identity Management, 3rd Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781284198362/files/images/9781284198355_CH01_FIGF01.png)